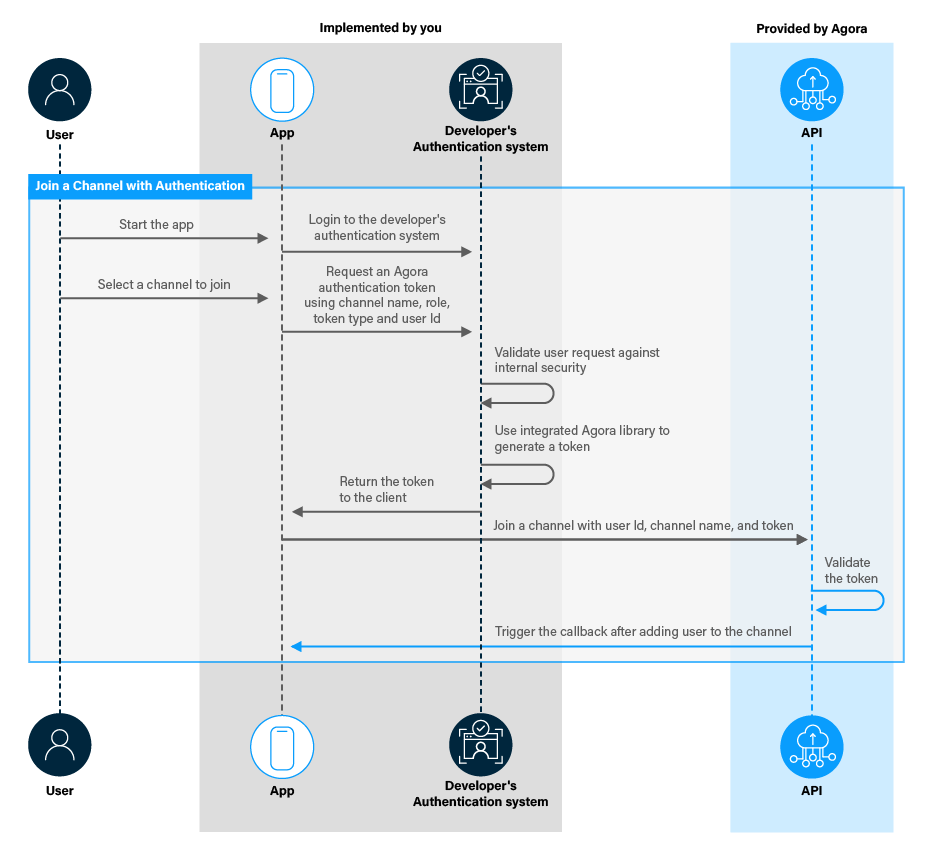
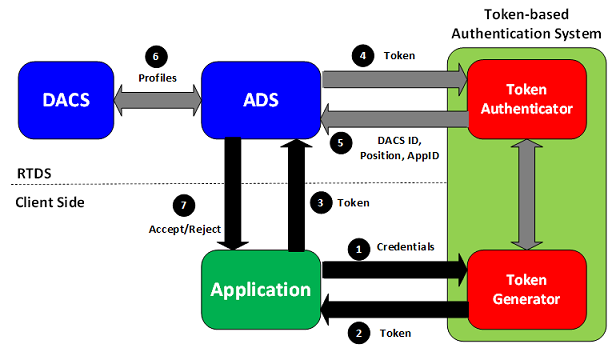
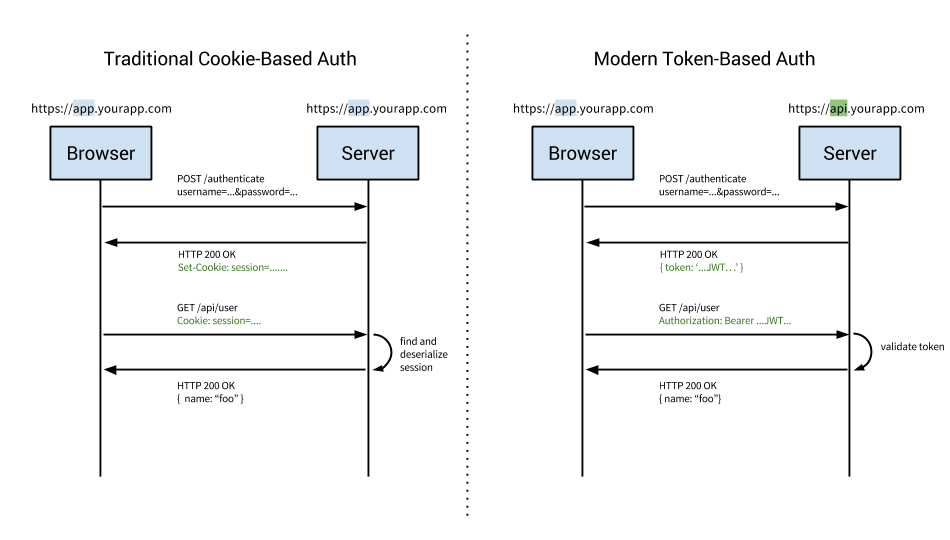
JWT - Authentication Token Key is not jhi-authenticationToken in sessionStorage · Issue #3235 · jhipster/generator-jhipster · GitHub

Examples of three hardware tokens, i.e., devices generating one-time... | Download Scientific Diagram

Human hand hold token generator with key for log on the system on computer laptop password protected. Vector illustration computer security with two factor authentication concept. Stock-Vektorgrafik | Adobe Stock